Dom Xss Payloads Hack Safe Automatically Finding Fixing Dom Based Xss Cross Site Scripting
Dom xss payloads Indeed lately has been hunted by consumers around us, maybe one of you. Individuals are now accustomed to using the net in gadgets to see video and image data for inspiration, and according to the name of the article I will discuss about Dom Xss Payloads.
- Adobe Robohelp 9 Dom Xss Security Assessment Title Adobe Robohelp 9 Dom Xss Author Roberto Suggi
- Intigriti Xss Challenge 4
- Convert Reflected Xss To Dom Based Xss To Bypass Length Limit Filter
- 2 Architecture Of Exploiting The Non Persistent Xss Attack 2 3 3 Download Scientific Diagram
- What Is Persistent Xss Acunetix
- Dom Xss Attack Exploitation Download Scientific Diagram
Find, Read, And Discover Dom Xss Payloads, Such Us:
- What Is Cross Site Scripting And How Can You Fix It
- Intigriti Xss Challenge 4
- Transforming Self Xss Into Exploitable Xss Netsparker
- Stored Reflected And Dom Based Xss Exploitation In Dvwa
- Password Stealing From Https Login Page And Csrf Protection Bypass With Reflected Xss By Michael Koczwara Medium
If you re looking for Dom Nad Rozlewiskiem you've arrived at the ideal location. We ve got 100 graphics about dom nad rozlewiskiem adding pictures, photos, pictures, backgrounds, and much more. In these page, we additionally provide variety of images available. Such as png, jpg, animated gifs, pic art, logo, blackandwhite, translucent, etc.
Xss is generated in client side by native continue reading dom based xss the 3 sinks.

Dom nad rozlewiskiem. Dom based xss vulnerabilities usually arise when javascript takes data from an attacker controllable source such as the url and passes it to a sink that supports dynamic code execution such as eval or innerhtml. Flaws that allow these attacks to succeed are quite widespread and occur anywhere a web application uses input from a user within the output it generates without validating or encoding it. Automated scanning scale dynamic scanning.
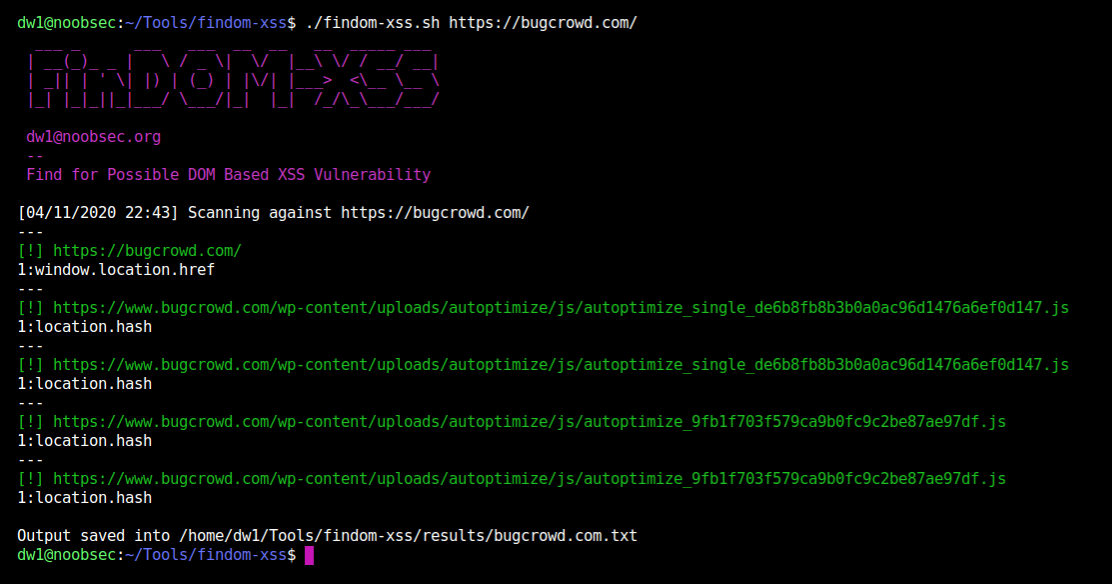
Application security testing see how our software enables the world to secure the web. How to detect dom xss. An easy way to test if your website or web application is vulnerable to dom based xss and other vulnerabilities is to run an automated web scan using the acunetix vulnerability scanner which includes a specialized dom based xss scanner module.
Xss attacks occur when an attacker uses a web application to send malicious code generally in the form of a browser side script to a different end user. This means that no data will be available in server logs. Bug bounty hunting level up your hacking and earn more bug bounties.
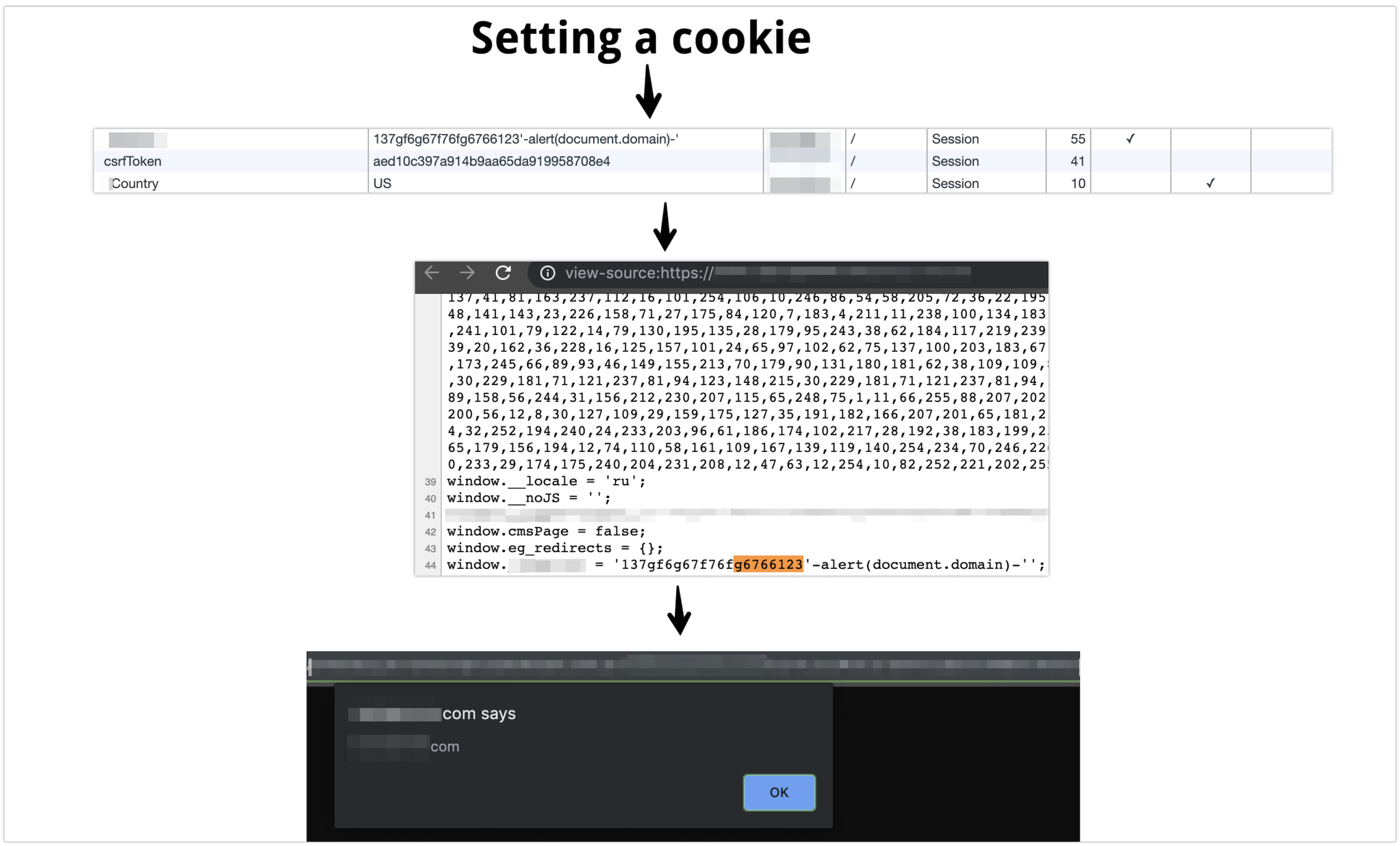
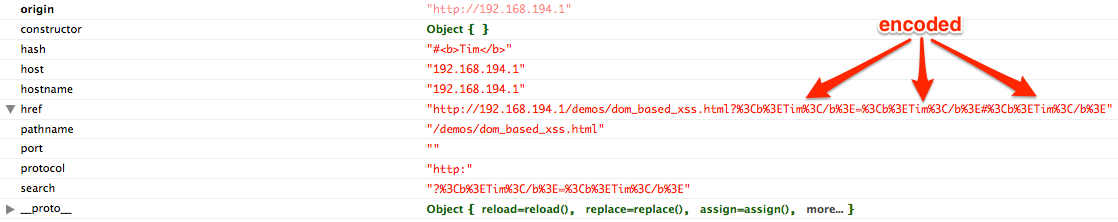
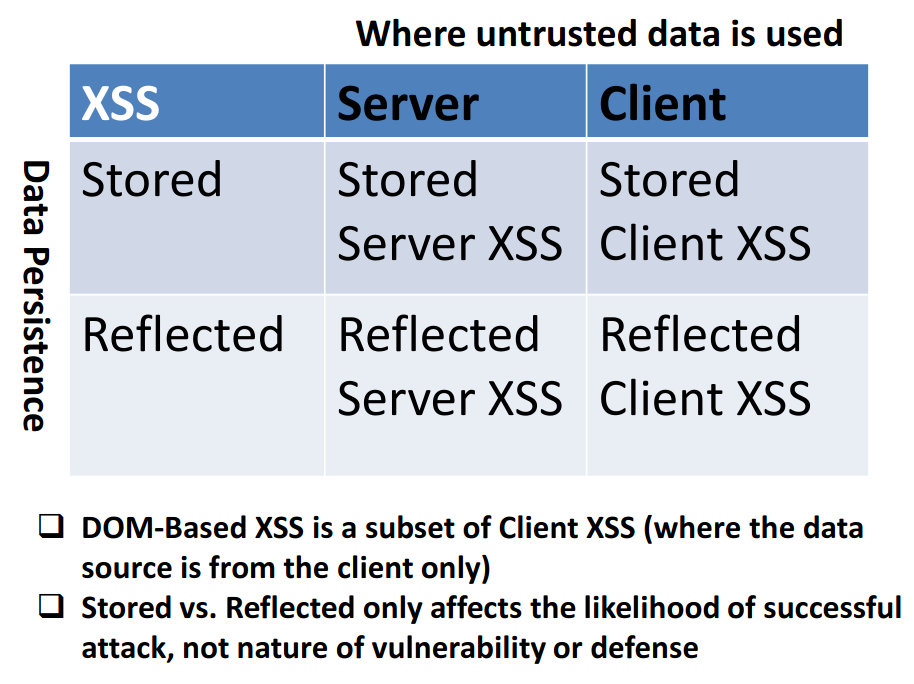
But theres another main type the dom based one where injected malicious input does not come from server via reflected or stored means. Dom based xss definition. In reflective and stored cross site scripting attacks you can see the vulnerability payload in the response page but in dom based cross site scripting the html source code and response of the attack will.
For more information about xss attacks see also. That is the page itself the http response that is does not. Xss payload list or cross site scripting xss attacks are a type of injection in which malicious scripts are injected into otherwise benign and trusted web sites.
It means that injected javascript code comes from server side to execute in client side. This fact makes it more difficult to maintain web application security. Most dom xss payloads are never sent to the server because they are prepended by the symbol.
It is almost impossible to detect dom xss only from the server side using http requests. Dom based xss and server interaction. With dom based xss the payload may or may not be delivered in the reply of the server but it will not be executed by the browser as is.
Instead the javascript code delivered by the server will take it and insert it into the dom thus leading to its execution. The most common type of xss cross site scripting is source based. Dom based xss or as it is called in some texts type 0 xss is an xss attack wherein the attack payload is executed as a result of modifying the dom environment in the victims browser used by the original client side script so that the client side code runs in an unexpected manner.
This enables attackers to execute malicious javascript which typically allows them to hijack other users accounts. Devsecops catch critical bugs. Dom based xss simply means a cross site scripting vulnerability that appears in the dom document object model instead of part of the html.
More From Dom Nad Rozlewiskiem
Incoming Search Terms:
- Hacking Castle Cross Site Scripting Xss Attack Info Tutorial And Prevention Dom Toretto Car,
- Hacking Castle Cross Site Scripting Xss Attack Info Tutorial And Prevention Dom Toretto Car,
- Highest Sql Injection And Xss Detection Rate Acunetix Dom Toretto Car,
- Xss 101 Brute Xss Dom Toretto Car,
- A Deeper Look Into Xss Payloads Digital Interruption Research Dom Toretto Car,
- Github Tegal1337 Xss Finder World S Most Powerful And Advanced Cross Site Scripting Software Dom Toretto Car,